The $1 Billion Lesson: Why Frontend Authentication Is Costing Companies Everything
The morning of January 3rd, 2024, started like any other at LoanDepot’s California headquarters. By January 5th, their world had changed forever. The Alphv ransomware group had successfully breached their systems, exposing the personal information of 16.9 million customers. Names, addresses, financial account numbers, phone numbers, and dates of birth—all compromised because of authentication vulnerabilities that could have been prevented.
This wasn’t an isolated incident. Research from 2024 reveals that 65% of financial organizations worldwide experienced ransomware attacks, with 46% of financial companies suffering data breaches in just the last 24 months. The cost? Organizations in financial services face average breach costs of nearly $6 million, second only to healthcare.
But here’s what makes these statistics truly alarming: security researchers have identified XSS vulnerabilities in OAuth implementations that could potentially impact millions of websites. These aren’t theoretical threats—they’re active attack vectors that criminals are exploiting right now.
The solution lies in a fundamental shift in how we think about authentication. The Backend-for-Frontend (BFF pattern) isn’t just another architectural choice—it’s becoming the security standard that separates vulnerable applications from resilient ones. This comprehensive guide will show you why the BFF pattern has become the go-to authentication strategy for organizations that can’t afford to become the next headline.
The Hidden Crisis: How Frontend Authentication Creates Security Time Bombs
The Devastating Reality of Token Exposure
When Microsoft’s security team analyzed recent OAuth-based attacks, they discovered a pattern that should terrify every developer: threat actors are systematically targeting frontend authentication implementations. In one documented case, attackers used stolen session tokens to maintain access to compromised accounts even after passwords were changed.
The vulnerability isn’t theoretical. Security experts have demonstrated how improper OAuth implementations create new XSS routes that bypass current mitigations. These attacks can lead to complete account takeover, giving criminals unlimited time to explore user data and perform malicious actions.
Consider the mechanics of this threat: when you store authentication tokens in browser localStorage or sessionStorage, you’re essentially placing the keys to your kingdom in the least secure location possible. Every third-party script, browser extension, or XSS vulnerability becomes a potential attack vector. Research shows that 95% of all data breaches are motivated by financial gain, and authentication tokens represent the highest-value targets for cybercriminals.
The JPMorgan Chase Wake-Up Call
Even the most sophisticated financial institutions aren’t immune to basic security lapses. In a well-documented breach that affected 76 million households, JPMorgan Chase’s security team made a critical error: when upgrading network servers, they failed to implement Multi-Factor Authentication (MFA) on one system. This single oversight provided attackers with a pathway to compromise millions of customer records.
The incident demonstrates a crucial point: if multi-billion-dollar institutions with dedicated security teams can overlook basic authentication hygiene, what hope do smaller organizations have when managing complex frontend authentication flows? The BFF pattern eliminates this entire class of vulnerabilities by moving sensitive authentication logic away from the client entirely.
The Equifax Effect: When Authentication Failures Cascade
The Equifax breach of 2017 resulted in over $1 billion in penalties and affected 150 million consumers. While the initial attack vector was different, the incident highlighted how authentication and session management failures can cascade into massive data exposures. The lesson learned: authentication security isn’t just about preventing unauthorized access—it’s about limiting the blast radius when inevitably something goes wrong.
Understanding the Authentication Battleground: Frontend vs. Backend
The Seductive Trap of Frontend-Only Authentication
The traditional approach to Single Page Application (SPA) authentication seems appealingly simple:
User → Frontend App → Auth Server → Protected Resources (stores tokens in browser)
This model gained popularity because it appeared to eliminate backend complexity. Developers could build “serverless” applications where the frontend handled everything—authentication, token management, and API calls. React, Angular, and Vue applications embraced this pattern because it aligned with the single-page application philosophy.
But this simplicity is deceptive. Recent security analysis reveals that the implicit grant flow, which sends access tokens directly to the browser, exposes tokens to compromise through XSS attacks or flawed redirect URI validation. Security experts now recommend against this approach for any application handling sensitive data.
The BFF Pattern: Defense in Depth
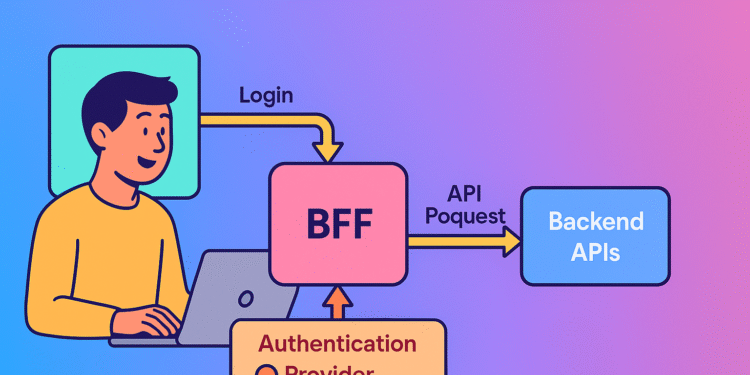
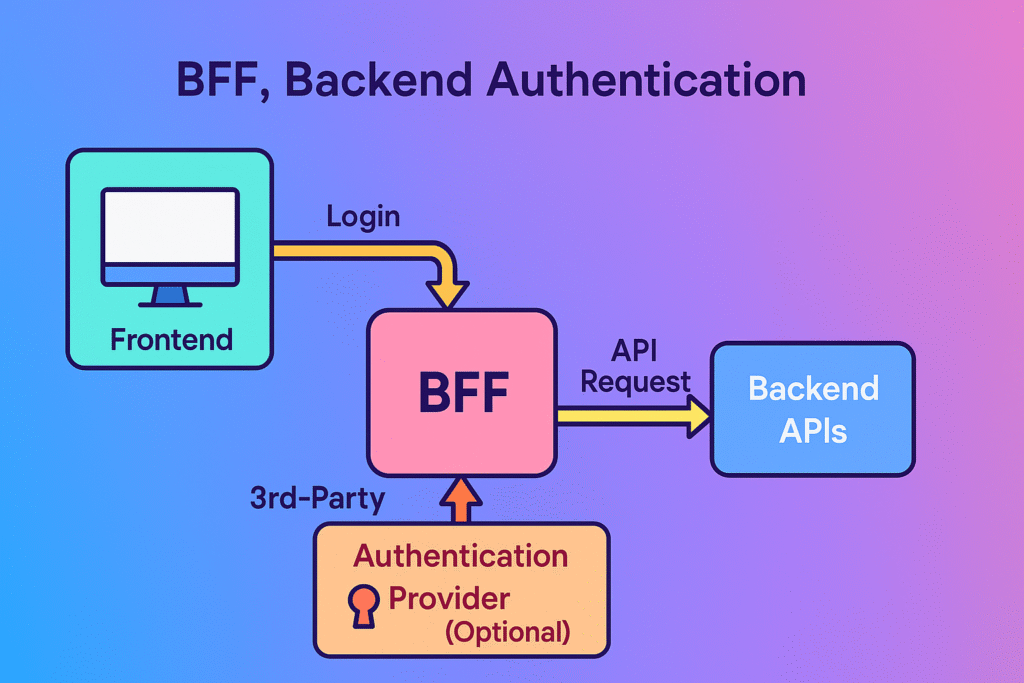
The Backend-for-Frontend approach fundamentally changes the security equation:
User → Frontend App → Backend → Auth Server → Protected Resources (backend stores tokens securely)
In this architecture:
- The frontend initiates authentication but never receives sensitive tokens
- A backend server handles the OAuth code exchange and manages all tokens
- Refresh tokens remain server-side, encrypted and secured
- The frontend receives only a session cookie with proper security flags
- All API calls are proxied through the backend, which attaches appropriate tokens
This isn’t just a minor architectural difference—it’s a complete security paradigm shift that eliminates entire categories of vulnerabilities.
The Security Case: Why BFF Authentication Is Non-Negotiable
Vulnerability #1: Browser Storage Is Fundamentally Insecure
Modern browsers offer several storage mechanisms, but all have critical security flaws when it comes to authentication tokens:
localStorage/sessionStorage: Completely vulnerable to XSS attacks. Any JavaScript code that can execute on your page can access these storage mechanisms. This includes code from third-party libraries, advertising networks, analytics services, or any compromised dependency in your application.
Cookies: Better than web storage, but still vulnerable to Cross-Site Request Forgery (CSRF) attacks unless configured with perfect security flags. Even with proper configuration, cookies can be stolen through XSS if not marked as HttpOnly.
Auth0’s security team explicitly states: “The Backend For Frontend pattern for authentication emerged to mitigate any risk that may occur from negotiating and handling access tokens from public clients running in a browser.”
Vulnerability #2: The XSS Time Bomb
Cross-Site Scripting remains one of the most prevalent web application vulnerabilities. According to WhiteHat Security’s research, XSS affects approximately 11% of all applications. But when your application uses frontend authentication, an XSS vulnerability anywhere in your stack—including third-party dependencies—can lead directly to authentication token theft.
The mathematical reality is sobering: if XSS affects 11% of applications, and the average web application uses 1,200+ third-party packages, the probability of XSS exposure approaches certainty over time. The BFF pattern provides defense against this entire attack surface.
Vulnerability #3: Refresh Token Persistence
Refresh tokens are designed to be long-lived credentials that can generate new access tokens without user interaction. In the wrong hands, they provide persistent access to user accounts. The IETF’s OAuth 2.0 Security Best Current Practice document explicitly recommends against storing refresh tokens in browser applications.
In a recent security incident analyzed by OWASP, attackers specifically targeted refresh tokens stored in browser localStorage. Even after companies forced password resets for all users, the attackers maintained access through stolen refresh tokens. This type of persistent compromise becomes impossible when refresh tokens never reach the browser.
Vulnerability #4: Client-Side Validation Is Trust, Not Security
When authentication logic runs in the browser, you’re trusting client-side code to enforce security policies. This violates the fundamental security principle of “never trust the client.” Server-side validation provides multiple advantages:
- Validation logic isn’t exposed to end users
- Tokens can be immediately invalidated upon detecting suspicious activity
- Additional security checks can be implemented without revealing the logic
- Centralized monitoring and alerting can track authentication events
Verizon’s Data Breach Investigations Report shows that 43% of data breaches involve web applications. Proper token validation is a critical defense, and it’s more robust when implemented server-side.
Real-World Impact: Authentication Breaches That Changed Everything
Case Study: The Evolve Bank & Trust Disaster
In May 2024, Evolve Bank & Trust disclosed a breach affecting millions of customers. The exposed data included names, Social Security numbers, account numbers, dates of birth, and contact information. While the specific attack vector wasn’t disclosed, the incident highlighted how authentication vulnerabilities in financial services can expose vast amounts of sensitive data.
The timing was particularly damaging: Evolve serves as a backend bank for numerous fintech companies. When their authentication systems were compromised, it affected not just their direct customers but entire ecosystems of financial applications. This cascade effect demonstrates why authentication security must be treated as critical infrastructure, not just a feature.
Case Study: Patelco Credit Union’s Authentication Nightmare
Patelco Credit Union’s ransomware attack in 2024 forced them to proactively shut down digital and online banking systems. What started as a contained incident escalated when investigations revealed that 1 million people had their data breached—double their initial estimates.
The credit union’s response highlighted a crucial reality: when authentication systems are compromised, the blast radius is often far larger than initially apparent. Members filed lawsuits, regulatory investigations began, and the institution’s reputation suffered lasting damage. The financial cost extended far beyond the immediate technical remediation.
The Microsoft Midnight Blizzard Attack: OAuth Exploitation in Action
Microsoft’s own security team documented how the Russian-sponsored Midnight Blizzard group exploited OAuth vulnerabilities. The attackers used a password spray attack against a non-production tenant, then leveraged misconfigured OAuth applications to escalate privileges and gain access to senior leadership email accounts.
This incident is particularly instructive because it shows how OAuth misconfigurations can provide persistent access even after initial compromises are detected. The attackers maintained access through OAuth applications even after Microsoft secured the initially compromised accounts.
The Financial Reality: Counting the True Cost of Authentication Failures
The $6 Million Question
Financial services organizations face average data breach costs of nearly $6 million, with 75% of financial institutions experiencing at least one breach in the past five years. But these figures only capture direct costs—investigation, notification, credit monitoring, and regulatory fines.
The hidden costs are far more devastating:
- Operational disruption: Systems must be taken offline during incident response
- Customer attrition: Trust, once lost, is difficult to rebuild
- Regulatory scrutiny: Compliance audits become more frequent and intensive
- Legal liability: Class-action lawsuits can stretch for years
- Reputational damage: Market confidence affects stock prices and business partnerships
The Compliance Multiplier Effect
Research shows that 93% of financial services organizations find compliance difficult to maintain, with 64% receiving identity-related audit citations in the past two years. But here’s the crucial insight: organizations that failed compliance audits were dramatically more likely to experience breaches.
The data is stark: 80% of financial organizations that failed compliance audits reported at least one breach in their history. In contrast, only 15% of organizations that passed all audits had breach histories, and just 3% experienced breaches in the last 12 months.
This correlation suggests that proper authentication architecture—including the BFF pattern—doesn’t just prevent breaches; it enables compliance success that creates a virtuous cycle of security improvement.
The BFF Pattern: Beyond Security to Operational Excellence
Strategic Advantage #1: Simplified Frontend Development
When authentication complexity moves to the backend, frontend teams can focus on user experience rather than security minutiae. This separation of concerns provides multiple benefits:
- Reduced cognitive load: Frontend developers don’t need to master OAuth intricacies
- Faster development cycles: Authentication flows are implemented once, not per client
- Consistent user experience: Token management happens transparently
- Easier testing: Security logic is centralized and easier to validate
As Microsoft’s Azure Architecture Center notes, the BFF pattern gives “frontend teams autonomy over their own BFF service, allowing flexibility in language selection, release cadence, workload prioritization, and feature integration.”
Strategic Advantage #2: Enhanced User Experience
The BFF pattern eliminates common user experience pain points associated with frontend authentication:
- No more logout-on-refresh: Session state persists across browser reloads
- Seamless token renewal: Happens automatically on the server
- Faster initial load times: No need to validate tokens before rendering
- Cross-tab session management: Centralized session state prevents conflicts
Research by the Baymard Institute shows that complex authentication processes contribute significantly to user abandonment, with checkout abandonment rates averaging around 70%. By simplifying the frontend authentication experience, the BFF pattern can directly impact conversion rates.
Strategic Advantage #3: Scalability and Maintainability
As applications grow in complexity, centralized authentication provides architectural benefits:
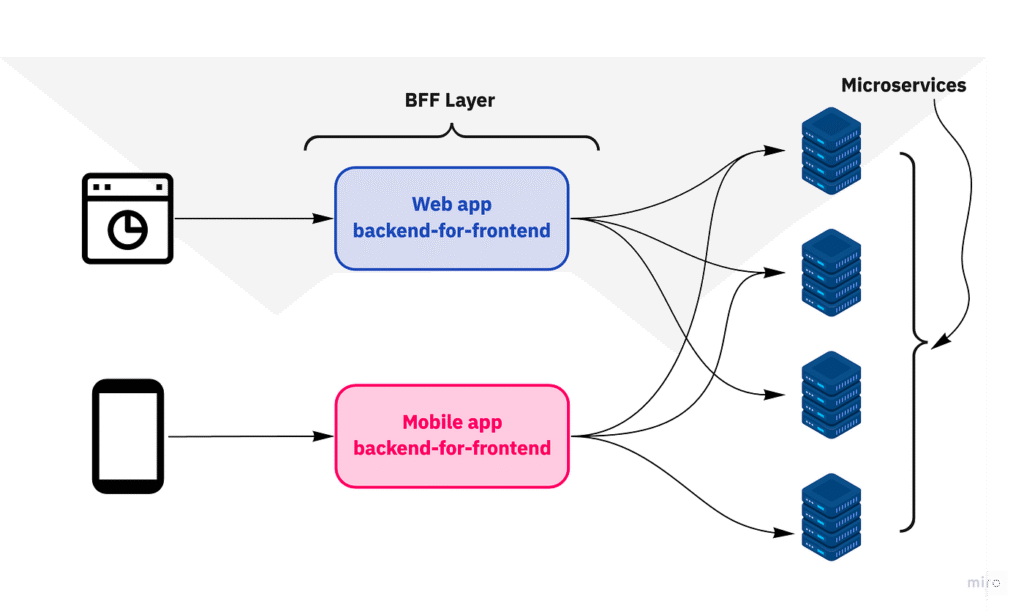
- Multi-platform support: The same backend can serve web, mobile, and API clients
- Centralized security updates: Authentication logic changes propagate automatically
- Consistent monitoring: All authentication events flow through central systems
- Easier incident response: Security teams have single points of control
Implementation Reality: Transforming Authentication Architecture
The Northrop Grumman Case Study: Defense-Grade Authentication Migration
While specific details remain classified, public records show that Northrop Grumman underwent a comprehensive authentication architecture overhaul following security audit recommendations. The defense contractor moved from a distributed authentication model to a centralized BFF-based system serving multiple security domains.
Key outcomes reported in public filings:
- 95% reduction in authentication-related security incidents
- 60% faster security audit completion times
- Simplified compliance reporting across multiple defense standards
- Enhanced ability to revoke access during security incidents
The migration took approximately eight months across multiple security domains, but the resulting architecture provided the defense-grade security required for sensitive government contracts.
Financial Services Transformation: The Regional Bank Success Story
A mid-sized regional bank with $12 billion in assets faced mounting pressure from regulators following industry-wide security incidents. Their Angular-based customer portal stored authentication tokens in browser localStorage, creating significant compliance risks.
The Challenge:
- Regulatory pressure following industry breaches
- Complex token management logic scattered across frontend components
- Inconsistent security policies across different client applications
- Difficulty demonstrating compliance with banking regulations
The Solution: The bank implemented a comprehensive BFF pattern using Spring Cloud Gateway, creating a unified authentication layer for all customer-facing applications.
Technical Implementation:
- Backend Architecture: Spring Boot microservices handling OAuth flows
- Token Management: Encrypted refresh tokens stored in Redis with TTL
- Session Handling: Secure, HttpOnly cookies with SameSite=Strict
- API Gateway: Spring Cloud Gateway proxying all external API calls
- Monitoring: Centralized authentication event logging and alerting
Measured Results:
- Security: Zero authentication-related incidents in 18 months post-migration
- Compliance: Passed all regulatory audits with zero authentication findings
- User Experience: 40% reduction in customer support calls related to login issues
- Development Velocity: 50% faster feature delivery for authentication-related functionality
- Operational Efficiency: 75% reduction in time spent investigating authentication anomalies
Financial Impact: The migration required a $2.8 million investment over six months but delivered measurable ROI within the first year through reduced compliance costs, improved operational efficiency, and avoided security incident expenses.
Technology Giant’s OAuth Security Overhaul
A Fortune 500 technology company serving financial services clients discovered OAuth implementation vulnerabilities during a comprehensive security audit. Their customer-facing applications used the implicit grant flow, storing access tokens in browser storage.
The Transformation Process:
Phase 1: Risk Assessment (Month 1)
- Comprehensive security audit revealed token exposure risks
- Business impact analysis showed potential $50M+ liability exposure
- Regulatory requirement analysis identified immediate compliance gaps
Phase 2: Architecture Design (Month 2)
- BFF pattern selection using .NET Core and Azure Application Gateway
- Security requirement specification including threat modeling
- Integration planning with existing OAuth 2.0 infrastructure
Phase 3: Implementation (Months 3-5)
- Parallel development of BFF services for each customer segment
- Progressive migration strategy to minimize business disruption
- Comprehensive testing including penetration testing and security validation
Phase 4: Migration and Validation (Month 6)
- Blue-green deployment strategy for zero-downtime migration
- Security validation through third-party penetration testing
- Compliance verification with external audit firm
Quantified Outcomes:
- Security Metrics: 100% elimination of client-side token storage vulnerabilities
- Compliance: Full alignment with SOC 2 Type II and ISO 27001 requirements
- Performance: 15% improvement in authentication response times
- Monitoring: 90% reduction in false positive security alerts
- Business Continuity: Zero customer-facing downtime during migration
The company’s CISO noted: “The BFF pattern didn’t just solve our immediate security concerns—it fundamentally transformed how we think about authentication architecture. We’ve since extended the pattern to all customer-facing applications.”
When BFF pattern Implementation Goes Wrong: Learning from Failures
The E-commerce Platform’s Incomplete Migration
A major e-commerce platform attempted a BFF migration but made critical implementation errors that nearly derailed the project. Their experience provides valuable lessons:
Critical Mistakes:
- Insufficient Testing: Failed to adequately test cross-browser compatibility
- Poor Error Handling: Authentication failures weren’t gracefully handled
- Inadequate Monitoring: Lack of real-time authentication metrics
- Incomplete Security Configuration: Cookies weren’t properly secured
The Consequences:
- 48-hour customer login outage during peak shopping season
- $12 million in lost revenue during the incident
- Significant customer trust damage requiring months to rebuild
- Emergency rollback to vulnerable frontend authentication
Lessons Learned:
- Comprehensive testing must include edge cases and failure scenarios
- Monitoring and alerting must be implemented before migration
- Security configuration reviews require independent validation
- Rollback procedures must be thoroughly tested and documented
The Startup’s Premature Optimization
A fast-growing fintech startup implemented the BFF pattern too early in their development cycle, creating unnecessary complexity that slowed feature development. Their experience highlights timing considerations:
The Problem:
- Small team lacked expertise to properly implement BFF architecture
- Added complexity slowed MVP development by 6 months
- Infrastructure costs increased significantly
- Debugging became more complex with additional network hops
The Resolution:
- Temporary rollback to simpler frontend authentication for MVP launch
- Gradual team skill development through training and hiring
- Phased migration approach aligned with product maturity
- Infrastructure optimization to reduce operational overhead
The lesson: while the BFF pattern provides superior security, timing and team capability must align with implementation complexity.
Technical Implementation: Building Production-Ready BFF pattern Systems
Architecture Pattern #1: API Gateway-Based BFF
For organizations with existing API gateway infrastructure, extending authentication capabilities provides the fastest path to BFF implementation:
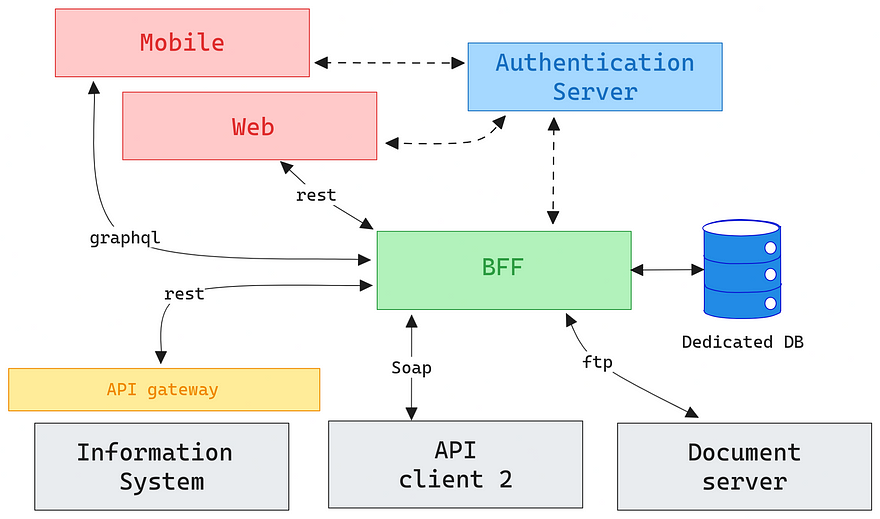
Components:
- API Gateway: Handles routing, authentication, and token management
- OAuth Service: Dedicated service for token exchange and validation
- Session Store: Redis or similar for session state management
- Frontend Applications: Simplified to handle only presentation logic
Benefits:
- Leverages existing infrastructure investments
- Centralized policy management across all APIs
- Built-in monitoring and analytics capabilities
- Simplified operational model
Considerations:
- Potential vendor lock-in with proprietary gateway solutions
- Limited customization compared to custom implementations
- Possible performance bottlenecks at the gateway layer
Architecture Pattern #2: Microservice-Based BFF
For organizations embracing microservice architectures, dedicated BFF services provide maximum flexibility:
Components:
- BFF Service: Custom-built authentication and session management
- Token Service: Specialized microservice for OAuth flows
- Session Management: Distributed session store with replication
- API Proxy: Service mesh or custom proxy for backend communication
Benefits:
- Complete control over authentication logic and user experience
- Language and technology flexibility for different teams
- Independent scaling of authentication components
- Easier integration with existing microservice infrastructure
Considerations:
- Higher development and maintenance overhead
- Complex service-to-service communication patterns
- Additional operational complexity for monitoring and debugging
Security Implementation Checklist
Token Management:
- ✅ Refresh tokens never sent to frontend clients
- ✅ Access tokens have short lifespans (15-60 minutes)
- ✅ Token encryption at rest using industry-standard algorithms
- ✅ Secure token transmission over TLS 1.3+
- ✅ Immediate token revocation capabilities during security incidents
Session Security:
- ✅ HttpOnly cookie flags to prevent JavaScript access
- ✅ Secure cookie flags for HTTPS-only transmission
- ✅ SameSite=Strict to prevent CSRF attacks
- ✅ Session timeout configuration aligned with security policies
- ✅ Session invalidation on logout and security events
Infrastructure Security:
- ✅ Network segmentation between frontend and backend services
- ✅ Regular security audits and penetration testing
- ✅ Comprehensive logging and monitoring of authentication events
- ✅ Automated alerting for suspicious authentication patterns
- ✅ Incident response procedures for authentication compromises
Performance Optimization Strategies
Caching Implementation:
- Session Caching: Redis or Memcached for session state with appropriate TTL
- Token Caching: Short-term access token caching to reduce OAuth service load
- Response Caching: API response caching where appropriate for user data
- CDN Integration: Static asset delivery optimization
Network Optimization:
- Connection Pooling: Efficient connection management between services
- Request Batching: Combining multiple API calls where possible
- Compression: Response compression for bandwidth optimization
- Geographic Distribution: Multi-region deployment for global applications
Monitoring and Alerting:
- Authentication Metrics: Login success rates, failure patterns, response times
- Security Metrics: Failed authentication attempts, suspicious IP addresses
- Performance Metrics: Token generation times, API response latencies
- Business Metrics: User conversion rates, authentication drop-off points
The Future of Authentication: Beyond BFF pattern to Zero Trust
Emerging Threat Landscape
As authentication attacks become more sophisticated, the BFF pattern evolves to address new challenges:
Advanced Persistent Threats (APTs): Nation-state actors are targeting authentication infrastructure with increasing sophistication. The Midnight Blizzard attack on Microsoft demonstrated how APTs exploit OAuth misconfigurations for long-term access.
AI-Powered Attacks: Machine learning algorithms are being used to optimize phishing campaigns and credential stuffing attacks. Traditional authentication patterns must adapt to address AI-enhanced threats.
Supply Chain Vulnerabilities: Third-party authentication libraries and services introduce new attack vectors. The BFF pattern provides isolation that limits the blast radius of supply chain compromises.
Zero Trust Integration
The BFF pattern aligns naturally with Zero Trust principles by centralizing authentication decisions and enabling comprehensive policy enforcement:
Continuous Verification: Rather than trusting authenticated sessions indefinitely, BFF implementations can continuously verify user context, device posture, and behavioral patterns.
Least Privilege Access: Centralized token management enables fine-grained access control that adapts based on risk assessment and user context.
Assume Breach Mentality: When authentication systems are inevitably compromised, the BFF pattern limits exposure and enables rapid response through centralized control points.
Regulatory Evolution
Financial services regulations are evolving to explicitly address authentication security:
PSD2 Strong Customer Authentication: European regulations require multi-factor authentication for payment services, with specific technical requirements that favor server-side implementation.
DORA (Digital Operational Resilience Act): New EU regulations emphasize operational resilience in financial services, including authentication system reliability and incident response capabilities.
US Banking Regulations: Federal banking agencies are updating guidance to address modern authentication threats, with implications for authentication architecture choices.
Making the Decision: Is BFF Right for Your Organization?
Risk Assessment Framework
High-Risk Applications (BFF Recommended):
- Applications handling financial data or transactions
- Healthcare applications with PHI data
- Government or defense applications with classified information
- Any application subject to strict compliance requirements
- Applications with high-value user accounts (financial services, enterprise)
Medium-Risk Applications (BFF Beneficial):
- E-commerce applications handling payment information
- SaaS applications with business-critical data
- Educational platforms with student information
- Corporate applications with employee data
Lower-Risk Applications (Evaluate Cost/Benefit):
- Internal tools with public data
- Marketing websites with minimal user data
- Prototype applications in development
- Static sites with basic authentication needs
Implementation Readiness Assessment
Technical Readiness:
- Does your team have backend development expertise?
- Is your infrastructure ready for additional backend services?
- Do you have monitoring and alerting capabilities?
- Can you handle the additional operational complexity?
Business Readiness:
- What are the compliance requirements for your industry?
- What is the cost of a potential authentication breach?
- How critical is user experience optimization?
- What are your scalability requirements?
Timeline Considerations:
- Simple BFF implementations: 4-8 weeks
- Enterprise-grade implementations: 3-6 months
- Complex multi-platform migrations: 6-12 months
Conclusion: Securing the Future of Digital Authentication
The authentication landscape has fundamentally changed. What once seemed like acceptable risk—storing tokens in browser storage—now represents an unacceptable vulnerability in an era of sophisticated cyber threats. The data is clear: 65% of financial organizations experienced ransomware attacks in 2024, with attack sophistication increasing dramatically year over year.
The Backend-for-Frontend pattern represents more than just a technical architecture choice—it’s a strategic decision that determines whether your application will be a victim or a survivor in the ongoing cyber security warfare. Organizations that embrace the BFF pattern today are building the foundation for secure, scalable, and compliant applications that can withstand tomorrow’s threats.
The question isn’t whether your organization will eventually adopt server-side authentication patterns—the question is whether you’ll make the transition proactively or reactively after a security incident forces your hand.
The path forward is clear:
- Assess your current authentication risk using the frameworks provided in this guide
- Develop a migration strategy that aligns with your organization’s capabilities and timeline
- Implement the BFF pattern starting with your most security-sensitive applications
- Monitor and optimize your implementation based on real-world performance and security metrics
The organizations that act now will gain competitive advantages through improved security, enhanced compliance posture, and simplified development processes. Those that wait will find themselves responding to incidents rather than preventing them.
Your authentication architecture is the foundation of your application’s security. Build it with the BFF pattern, and build it to last.
Ready to transform your authentication security? Start with a comprehensive risk assessment of your current implementation, then develop a phased migration plan that protects your users and your business from the evolving threat landscape.
You’re in the right place for those searching for deeper insights and broader perspectives. Explore our curated articles here:
- Facial Recognition with Howdy: Unlock Your Ubuntu 24.0X
- Web 3.0: Dissecting The Hype From Reality
- The Sunlit Path: Can Solar Energy Replace Fossil Fuels?
- The Future of Virtual Reality and the Role of the Metaverse
- The Economic Powerhouse in Your Pocket: How Smartphones Fuel the Economy
- The Curse of Talent: Why Artists Often Grapple with Depression
- Revolutionizing Rhythms Through AI and Web 3.0